Trusted shipping
Easy returns
Secure shopping
- Clothing, Shoes, Jewelry & Watches
- Home, Garden, Outdoor & Pets
- Electronics
- Audio, Video & Portable Devices
- Cables
- Adapters & Gender Changers
- Headsets, Speakers & Soundcards
- Power Protection
- 3D Printing
- Video Cards & Video Devices
- Tools & Components
- Sound Cards
- Alternative Energy
- Barebone / Mini Computers
- SSDs
- Accessories
- Mobile Accessories
- Storage Devices
- Personal Care
- Healthcare
- Home Theatre Systems
- Laptops, Computers & Office
- Speakers & Audio Systems
- Tech Services & Support
- Projectors, TVs & Home Theater
- Wi-Fi & Networking
- Cell Phones
- Electronics Deals
- Headphones
- Tablets & E-Readers
- Digital Cameras
- Home Phones
- Tech Accessories
- Electronics Sanitizing & Cleaning Supplies
- Smart Home
- Batteries, Power Banks & Chargers
- Wearable Technology
- GPS & Navigation
- Movies, Music, Books & Games
- Luggage
- Bible Covers
- Briefcases
- Camo
- Coolers
- Toiletry Bags
- Tote Bags
- Backpacks
- Carry-on Luggage
- Checked Luggage
- Lunch Bags
- Travel Accessories
- Luggage Deals
- Laptop Bags & Briefcases
- Kids' Luggage
- Duffels & Gym Bags
- Suitcases
- RFID Blocking Luggage & Travel Accessories
- Luggage Sets
- Mens' Luggage
- Handbags
- Accessories
- Outdoor
- Beauty Luggage
- Travel Totes
- Garment Bags
- Weekenders
- Messenger Bags
- Beauty & Health
- Category List
- Clothing, Shoes, Jewelry & Watches
- Home, Garden, Outdoor & Pets
- Electronics
- Audio, Video & Portable Devices
- Cables
- Adapters & Gender Changers
- Headsets, Speakers & Soundcards
- Power Protection
- 3D Printing
- Video Cards & Video Devices
- Tools & Components
- Sound Cards
- Alternative Energy
- Barebone / Mini Computers
- SSDs
- Accessories
- Mobile Accessories
- Storage Devices
- Personal Care
- Healthcare
- Home Theatre Systems
- Laptops, Computers & Office
- Speakers & Audio Systems
- Tech Services & Support
- Projectors, TVs & Home Theater
- Wi-Fi & Networking
- Cell Phones
- Electronics Deals
- Headphones
- Tablets & E-Readers
- Digital Cameras
- Home Phones
- Tech Accessories
- Electronics Sanitizing & Cleaning Supplies
- Smart Home
- Batteries, Power Banks & Chargers
- Wearable Technology
- GPS & Navigation
- Movies, Music, Books & Games
- Luggage
- Bible Covers
- Briefcases
- Camo
- Coolers
- Toiletry Bags
- Tote Bags
- Backpacks
- Carry-on Luggage
- Checked Luggage
- Lunch Bags
- Travel Accessories
- Luggage Deals
- Laptop Bags & Briefcases
- Kids' Luggage
- Duffels & Gym Bags
- Suitcases
- RFID Blocking Luggage & Travel Accessories
- Luggage Sets
- Mens' Luggage
- Handbags
- Accessories
- Outdoor
- Beauty Luggage
- Travel Totes
- Garment Bags
- Weekenders
- Messenger Bags
- Beauty & Health
- Baby & Toys
- Sports & Outdoors
- School & Office Supplies
- Breakroom & Janitorial Supplies
- Diaries
- Utility & Stationary
- Pens & Pencils
- Teacher Supplies & Classroom Decorations
- Paper
- Markers
- Binders
- School Supplies
- Packing & Mailing Supplies
- Tape, Adhesives & Fasteners
- Boards & Easels
- Crayons
- Desk Organization
- Pencils
- Filing & Organizers
- Journals
- Pens
- Labels & Label Makers
- Tools & Equipment
- Calendars
- Sticky Notes
- Notebooks
- Erasers & Correction Tape
- Pencil Cases
- Planners
- Retail Store Supplies
- Highlighters
- Locker Accessories
- Cute School Supplies
- School & Office Accessories
- Food & Grocery
- Shops All
- Unique-Bargains
- Cool cold
- Wesdar
- i-Star
- CoCoCo
- Targus
- Cooling Device Accessories
- Xtrike Me
- Tech/Gaming
- Gift Cards
- Women's Accessories
- Flash
- Men's Clothing
- Gift Ideas
- Brand Experiences
- Sale on Select School & Art Supplies
- Jewelry
- Featured Brands
- Nursing Items
- Storage
- Men's Shoes
- College
- School & Office Supplies
- Bullseye's Playground
- PRIDE
- Women's and Men's Shoes & Accessories
- Holiday Trees, Lights & More Sale
- Women's Dresses
- Gingerbread
- Caregiver Essentials
- Baby Bath
- select School Supplies
- Doorbusters
- Bedding & Bath
- Women's Sandals
- Sandals for the Family
- Men's Accessories
- Shops All
- One-day Easter sale
- select Health Items
- Friendsgiving
- Women's Tops, Shorts & Shoes
- Made By Design Organization
- Baby Mealtime
- For New & Expecting Parents
- Crayola Kids' Daily Deal
- Spritz Party Supplies
- Wellness Icon Glossary
- Our Generation Dolls & Accessories Kids' Daily Deal
- select Home items
- Mas Que
- Baby Apparel
- Children's Board Books Kids' Daily Deal
- Select Office Furniture
- Most-added Wedding Registry Items
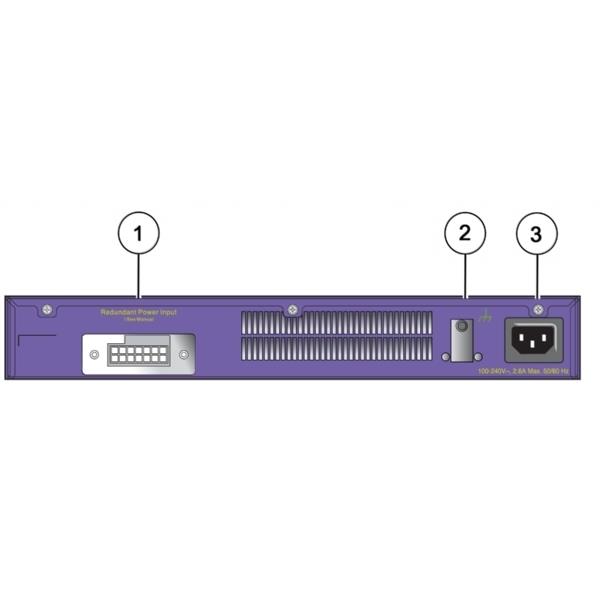
Buy Extreme Networks, Inc 16701 X460-G2-24t-10GE4 Base Unit in United States - Cartnear.com
Extreme Networks, Inc 16701 X460-G2-24t-10GE4 Base Unit
CTNR1171014 0644728167012 CTNR1171014Extreme Networks
2027-03-01
/itm/extreme-networks-inc-16701-x460-g2-24t-10ge4-base-unit-1171014
USD
4753.82
$ 4,754 $ 4,851 2% Off
Item Added to Cart
customer
*Product availability is subject to suppliers inventory
SHIPPING ALL OVER UNITED STATES
100% MONEY BACK GUARANTEE
EASY 30 DAYSRETURNS & REFUNDS
24/7 CUSTOMER SUPPORT
TRUSTED AND SAFE WEBSITE
100% SECURE CHECKOUT
- The Summit® X460-G2 series is based on Extreme Networks® revolutionary Extreme
XOS®, a highly resilient OS that providescontinuous uptime, manageability and operational efficiency. Each switch offers the same high-performance, nonblocking hardware technology, in the Extreme Networks tradition of simplifying network deployments through the use of common hardware and software throughout the network.
The Summit X460-G2 switches are effective campus edge switches that support Energy Efficient Ethernet (EEE - IEEE 802.3 az) with IEEE 802.3 at PoE-plus and can also serve as aggregation switches for traditional enterprise networks. The Summit X460-G2 series is also an option for DSLAM or CMTS aggregation, or for active Ethernet access.
The Summit X460-G2 can also be used as a top-of-rack switch for many data center environments with features such as high-density Gigabit Ethernet for concentrated data center environments; XNV™ (Extreme
XOS Network Virtualization) for centralized network-based Virtual Machine (VM) inventory, VM location history and VM provisioning; Direct Attach™ to offload VM switching from servers, thereby improving performance; high-capacity Layer 2/Layer 3 scalability for highly virtualized data centers; and intra-rack and cross-rack stacking with industry-leading flexibility.
Comprehensive Security Management- User policy and host integrity enforcement, and identity management
- Universal Port Dynamic Security Profiles to provide fine granular security policies in the network
- Threat detection and response instrumentation to react to network intrusion with CLEAR-Flow Security Rules Engine
- Denial of Service (DoS) protection and IP security against man-in-the-middle and DoS attacks to harden the network infrastructure
- Role Based Policy enables support for policy profiles to secure and provision network resources based upon the role the user or device plays within the network.